Starting out? Start with Cyber 101!
In selecting the right penetration testing partner, it’s crucial to go beyond superficial checks. To ensure that the chosen firm can adequately meet your needs.
Here are the 7 key factors to consider.
1. Understanding of Your Business Context
A penetration testing partner must do more than just “run the tools.” They need to comprehend your business context, risks, and goals. Are you prioritizing compliance, or is your primary concern understanding potential lateral movement within your internal network? The right partner should adapt their testing methodologies to match your unique environment. Avoid firms that take a cookie-cutter approach—their lack of contextual understanding could lead to missed risks or irrelevant findings.
Beware of companies that brand their service as a “penetration test” but merely run vulnerability scanners. These scans alone provide a surface-level analysis and lack the depth of a true penetration test. A proper penetration test requires skilled testers who can manually probe and validate findings, ensuring that all potential risks are uncovered.
2. Consider a real-world scenario
We were tasked with performing a penetration test for a client who initially relied on automated Nessus scans for their security posture. While effective at identifying many common vulnerabilities, Nessus missed various SQL Injection vulnerabilities (out-of-band and blind-boolean).
Our manual testing approach identified this overlooked issue, and to demonstrate its severity, we developed a formal Proof of Concept (PoC).
The outline of this vulnerability with the following payload using Burp Collaborator to pull a database name.


However, upon further investigation, we also found a blind-boolean injection vulnerability. A true statement returns an HTTP 200 (OK) response regardless of whether our token is valid; this indicates an unauthenticated SQL injection vulnerability (HTTP 403 forbidden if false).
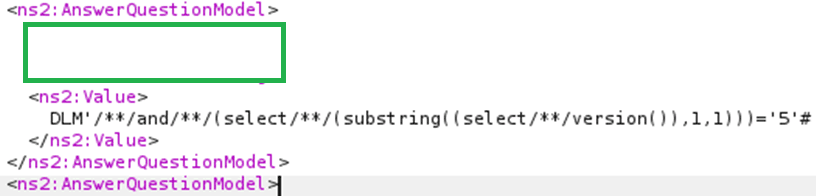
Due to the intricacies of this injection surface, scripting the vulnerability made it easy to extract the full MySQL version of 5.7.12 along with the db_name to illustrate a critical severity.
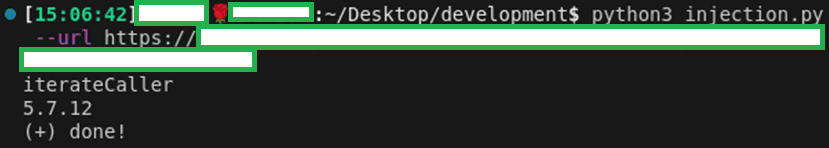
This custom PoC successfully extracted all database names, highlighting the real risk to the organization. The following is an extract of the custom script

This comparison emphasizes the importance of human expertise and understanding the unique intricacies of an environment—something that goes beyond just running automated tools.
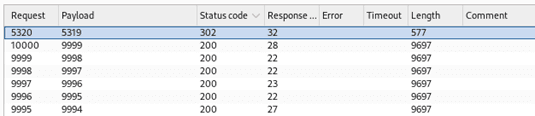
This is one of many examples highlighting the importance of vulnerabilities that scanners often fail to detect. Other examples may include bypassing MFA due to the lack of throttling or the MFA code being exposed to the client being challenged. For example, the 302 redirect indicates a valid code:
3. Qualifications and Certifications
Qualifications do matter. An experienced team backed by industry-recognized certifications such as OSCP, OSWE, or CREST membership ensures they adhere to well-defined standards of testing. However, just a badge isn’t enough—experience trumps certifications when it comes to uncovering those subtle, nuanced vulnerabilities that automated tools may miss. Ask questions about their experience, especially if your organization has niche requirements, like specific tech stacks or legacy systems.
4. Methodology and Reporting Standards
Not all penetration tests are the same. Ensure your partner uses a comprehensive and transparent testing methodology—ideally one based on standards like the OWASP Testing Guide. Good testers will lay out their approach, clarify how they identify and validate vulnerabilities, and adapt based on how your systems react during engagement. Also, reporting is key. A report full of raw tool output is useless if it doesn’t give you actionable insights. Look for testers who can translate technical vulnerabilities into business risk and offer clear remediation advice.
5. Communication Style
Effective penetration testing is a collaborative effort. Throughout the engagement, testers will need to work closely with your internal teams, often dealing with sensitive information or system disruptions. Look for a partner with good communication skills who’s willing to clarify findings, discuss recommendations, and help your team remediate issues. Red flags include poor communication or an overly complex style—they should be able to break down even the most intricate exploit path in a way that makes sense to both technical and business stakeholders.
6. Price vs. Value
Quality penetration testing services aren’t cheap, but the cost of an inadequate test can be far greater. While you should work within your budget, choosing a partner solely based on the lowest bid is often counterproductive. Consider the value they provide: Are they uncovering deep systemic issues? Do they offer meaningful remediation support? Quality comes with experience, skill, and effort—investing a bit more can save you headaches (and money) in the long run.
7. References and Case Studies
Ask for references and case studies. A reputable partner will have testimonials or previous success stories they can share (within confidentiality bounds). Understanding how they’ve helped similar businesses can provide insights into their capabilities and help gauge whether they’re a good fit for your specific needs.
Conclusion
Choosing a penetration testing partner requires careful consideration of both technical and business factors. The right partner won’t just identify vulnerabilities; they’ll also understand the nuances of your business, communicate effectively, and help elevate your security posture. Be selective—remember, the aim is to prevent a breach, not just tick a compliance checkbox. Ultimately, penetration testing should be viewed as a security investment, rather than just an expense.
